PEER-TO-PEER BOTNETS
A SURVEY ON PROPAGATION, DETECTION AND DETECTION EVASION TECHNIQUES
Keywords:
Peer-to-Peer Botnets, Evasion Techniques, Malware, Adversarial Attacks, Botnet DetectionAbstract
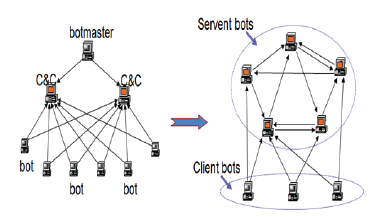
Botnets have been identified as one of the major threats to users in the internet space, nowadays. Unlike other categories of malware, botnets use Command and Control channels to launch and propagate their attacks. These botnets have been classified as centralised and decentralised (Peer-to-Peer). Due to the structure, Peerto-Peer botnets have different behavioural characteristics from centralised botnets. Past researches have equally identified that Peer-to-Peer botnets are more difficult to detect and shutdown compared to centralised botnets. This work provides a survey on the propagation, detection and detection evasion techniques of Peerto-Peer botnets. The study was able to identify various machine learning-based classifiers that have been proposed to detect Peer-to-Peer botnets in the cyber space. It is believed that any identified gap in the detection mechanisms will bring better insights into P2P botnet researches. The work concluded that identifying some of the Peer-to-Peer botnet propagation mechanisms and their detection evasion techniques will enable security researchers and experts to come up with improved botnet identification and mitigation approaches.
Downloads