Improved Security Techniques in Multi-Protocol Label Switching
Keywords:
MPLS, Network Security, computer networks, MPLS VPN, MPLS AuthenticationAbstract
Multi-Protocol Label Switching has replaced Layer 2 ATM and Frame Relay technology for a while now, which provides high speed networking and traffic engineering. MPLS technology uses Label switching technique instead of IP routing when forwarding traffic to a destination, which makes it more scalable and flexible. However IP MPLS networks are not secure from outside threats and threats from within the network. In this paper, inherent security provided by a typical MPLS network is evalu-ated, and some combinations of
security techniques are provided to improve upon it. To test some of the methods for enhancing the security of IP MPLS VPN network, two major attacks were carried out, i.e. Injection of IPv4 Routing Information, and Cracking of MD5 password with Authentication set to OFF and ON respectively. In order to protect the confidentiality, availability and integrity of data, in-herent security can be enhanced using step-by-step combination of the security techniques such as IP-Sec tunnels at the Customer Edge’s routers and a complex
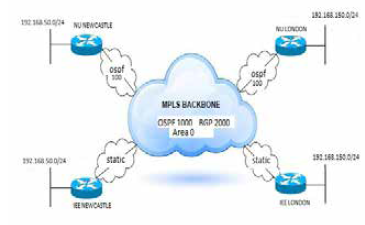
MD5 authentication between routing proto-cols. The MPLS network design was carried out to capture two locations in the UK, i.e. Newcastle and London. GNS3 Network emulator was used to achieve the desired results, with real Cisco IOS images, and finally, some thoughtful recommendations were provided, which are aimed at providing a better implementation of MPLS VPN on computer networks.
Downloads